What is Active Directory?
Written by Wyatt Melin on 6/16/24
If I were to explain Active Directory to my grandpa, who made maps in WWII, I would say that Active Directory (AD) is like a detailed map of a network that shows how users, computers, and other resources are connected and organized. Imagine a big map with different regions and landmarks, where each region represents a group of users or devices, and the landmarks are the resources like printers or shared files.
Just as a cartographer carefully marks out cities, rivers, and borders on a map, AD allows administrators to define and manage users and devices, set up access rules, and ensure everything is in its place. For example, much like labeling different regions for different purposes on a map, AD can organize users into groups (like departments) and set rules about who can access what.
So, grandpa, if you are reading this, while AD might seem like a simple map at first glance, it’s actually a labyrinth of settings and rules that can trip you up if you’re not careful. And just like in your map-making days, one tiny mistake can lead to a whole lot of unexpected adventures!
Before we can understand how to exploit Active Directory, we must first understand active directory concepts that we need to exploit.
Understanding Active Directory for Exploitation.
1. Domains, Trees, and Forests:
- Domain: This is like a city on your map. It’s a grouping of users, computers, and other resources that share a common directory database. Each domain has its own set of rules and security policies.
- Tree: Imagine several cities connected by roads and sharing a common theme or purpose. In AD, a tree is a collection of domains that are linked in a hierarchical manner, sharing a contiguous namespace.
- Forest: This is like a large country made up of several interconnected cities and regions. A forest is a collection of trees that share a common global catalog and directory schema.
2. Organizational Units (OUs):
- These are like neighborhoods or districts within a city. OUs are used to organize users, computers, and other objects into manageable units. Administrators can apply policies to OUs to control the behavior of the objects within them.
3. Users and Groups:
- Users: These are the individual citizens in our map analogy. Each user has a unique identity and can have various permissions to access resources.
- Groups: Think of these as clubs or organizations within the city. Groups allow for easier management of permissions. Instead of assigning permissions to each user individually, you can assign them to a group, and all members of the group inherit those permissions.
4. Domain Controllers (DCs):
- These are the government buildings or control centers in our city analogy. DCs are servers that store a copy of the AD database and manage the authentication and authorization of users and devices.
5. Global Catalog (GC):
- Consider the GC as the master index of the map. It’s a distributed data repository that contains a searchable, partial representation of every object in the AD forest. The GC enables users to find resources across domains quickly.
6. Trusts:
- Trusts are like diplomatic relations between cities or countries. They define how domains trust each other to share resources. For example, if Domain A trusts Domain B, users from Domain B can access resources in Domain A according to the permissions granted.
7. Group Policy:
- Think of Group Policy as the laws and regulations of the city. Group Policy allows administrators to define and enforce rules and configurations for users and computers. For example, you can use Group Policy to enforce password policies, install software, and configure settings on users’ computers.
8. Schema:
- The schema is like the legend or key on a map. It defines the types of objects and the attributes they can have within the AD. For instance, the schema dictates what information can be stored about a user (e.g., name, email, phone number).
9. DNS (Domain Name System):
- DNS is like the map’s address system. It translates user-friendly domain names (like www.example.com) into IP addresses that computers use to locate each other on the network. AD relies heavily on DNS to function correctly.
Understanding Active Directory for Exploitation.
1. Moving Laterally
In Active Directory (AD), moving laterally refers to transferring an object between Organizational Units (OUs) that are at the same level in the directory hierarchy. For example, moving a user from the “Sales” OU to the “Marketing” OU.
Examples of Moving Laterally:
When users or objects are moved from one department OU to another without adjusting their access rights and permissions accordingly.
Why it’s a Weakness:
- Access Control Issues: Moving objects laterally can disrupt established access controls. For instance, if a user from “Sales” with specific access rights is moved to “Marketing,” they might inadvertently retain access to sales resources or gain unintended access to marketing resources, leading to potential data breaches.
- Policy Conflicts: Different OUs may have different security policies and configurations. Moving a user laterally can result in conflicting policies being applied, potentially weakening the overall security posture.
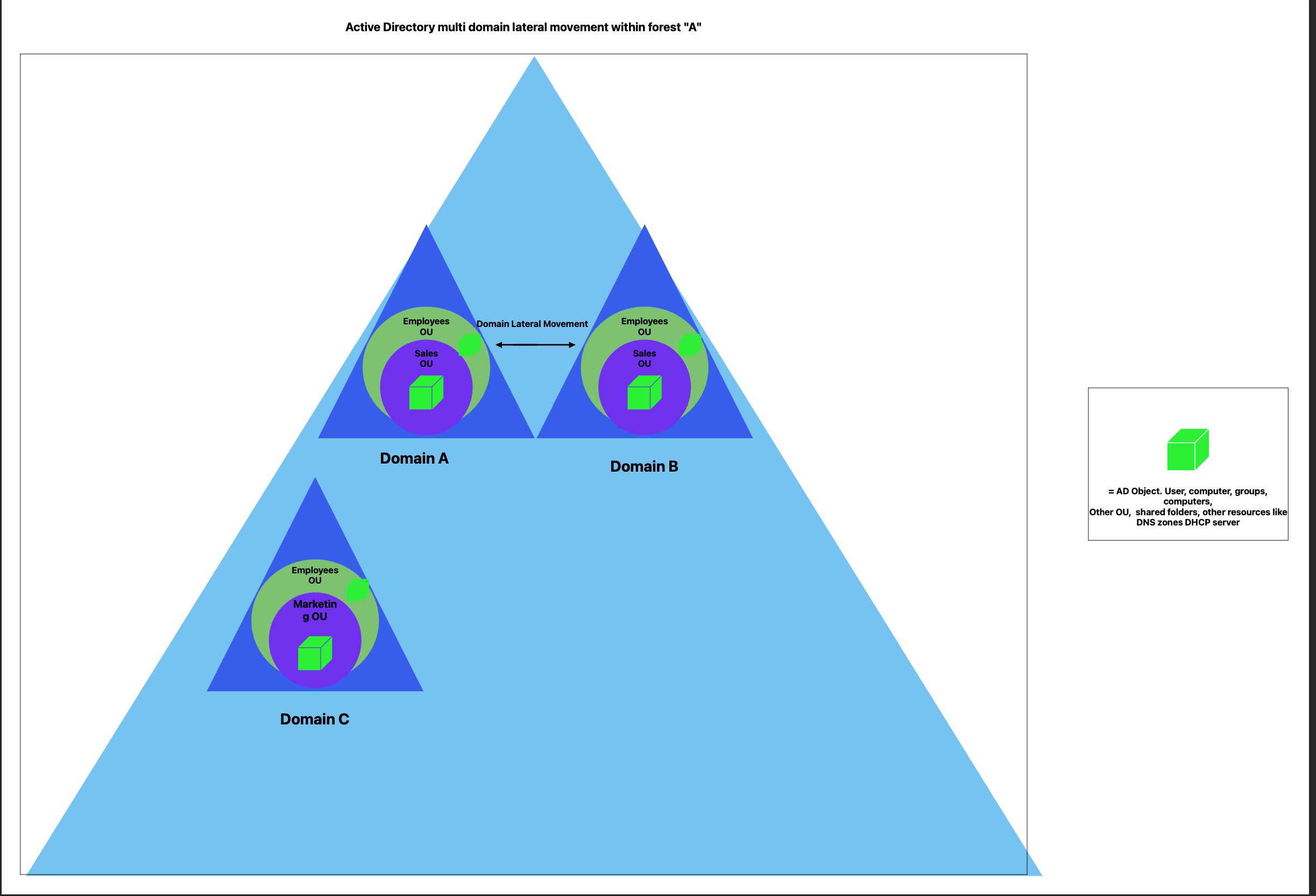 This diagram illustrates the structure of the Active Directory forest "A", showing three domains: "A", "B", and "C". Each domain contains organizational units (OUs) such as Employees and Sales or Marketing, with AD objects like users, computers, and groups represented by green cubes. The arrows between "A" and "B" domains signify the potential for lateral movement of AD objects between domains within the forest.
This diagram illustrates the structure of the Active Directory forest "A", showing three domains: "A", "B", and "C". Each domain contains organizational units (OUs) such as Employees and Sales or Marketing, with AD objects like users, computers, and groups represented by green cubes. The arrows between "A" and "B" domains signify the potential for lateral movement of AD objects between domains within the forest.
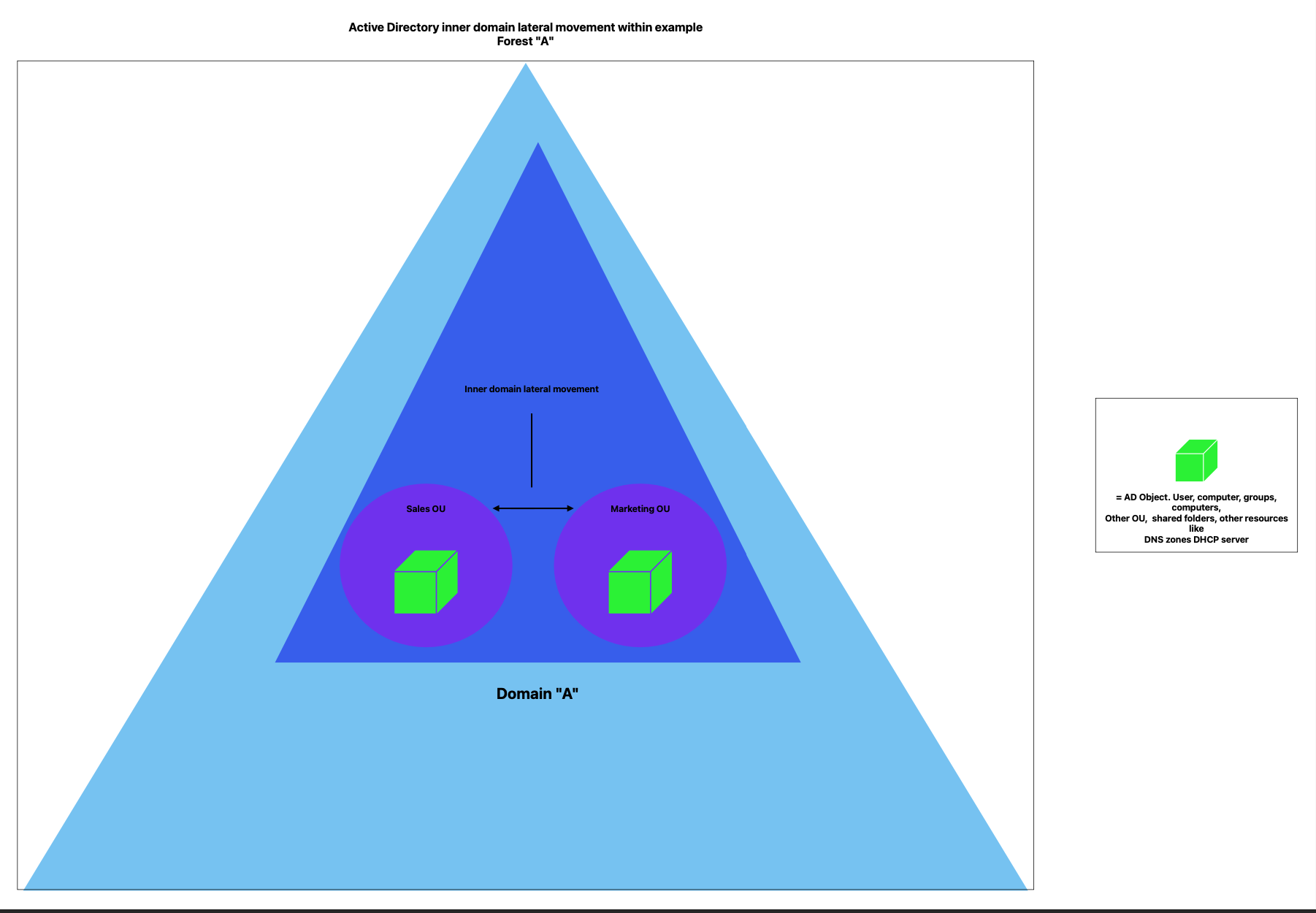 This diagram represents the internal structure of the "A" domain in the Active Directory forest. It shows the Sales and Marketing Organizational Units (OUs) within the domain, each containing Active Directory objects (depicted as green cubes). The arrows indicate potential paths for lateral movement of these objects within the same domain, highlighting the interactions and access that objects in different OUs may have with each other. This emphasizes the importance of securing and monitoring internal movement to prevent unauthorized access and maintain security within the domain.
This diagram represents the internal structure of the "A" domain in the Active Directory forest. It shows the Sales and Marketing Organizational Units (OUs) within the domain, each containing Active Directory objects (depicted as green cubes). The arrows indicate potential paths for lateral movement of these objects within the same domain, highlighting the interactions and access that objects in different OUs may have with each other. This emphasizes the importance of securing and monitoring internal movement to prevent unauthorized access and maintain security within the domain.
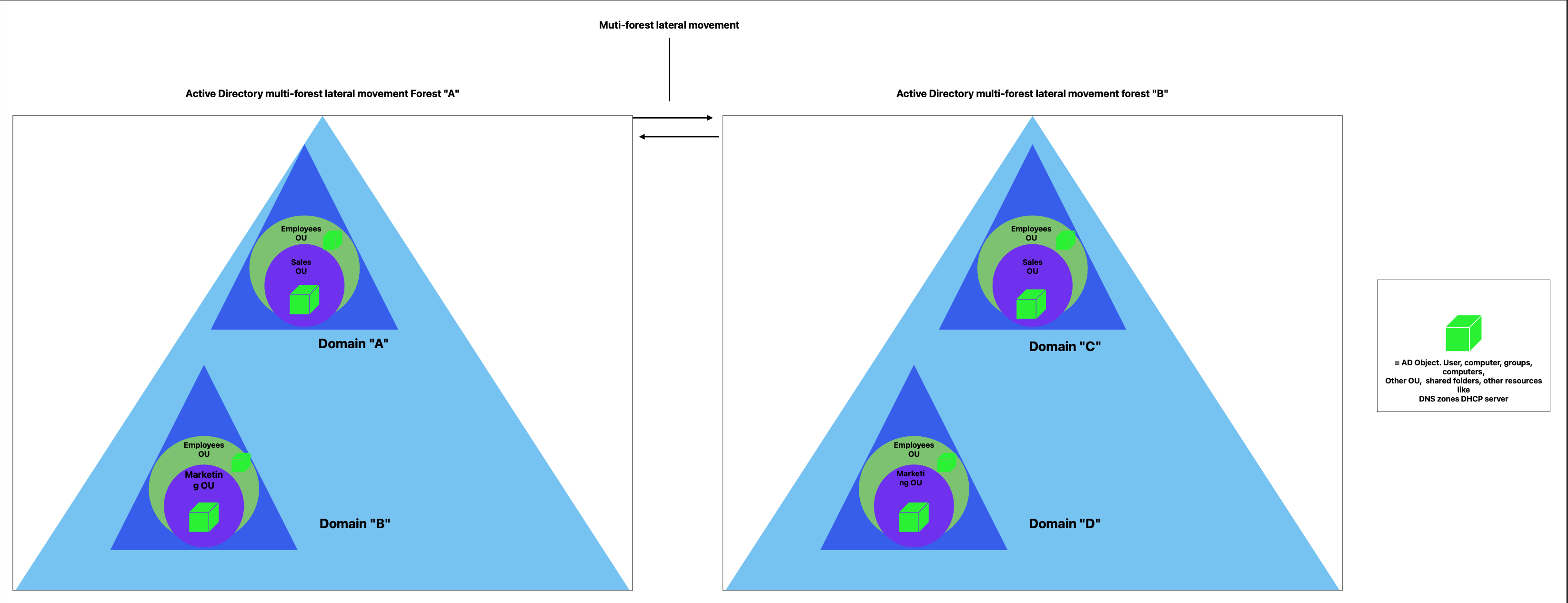 This diagram demonstrates the concept of multi-forest lateral movement between two separate Active Directory forests: "A" and "B". Each forest contains multiple domains ("A" with "B", and "C" with "D"), each domain hosting its own Organizational Units (OUs) like Employees, Sales, and Marketing. The green cubes represent various AD objects such as users, computers, and groups. The arrows indicate the potential for lateral movement of these objects both within domains of the same forest and across domains in different forests. This highlights the complexities and security considerations when managing multiple forests and ensuring secure interactions between them.
This diagram demonstrates the concept of multi-forest lateral movement between two separate Active Directory forests: "A" and "B". Each forest contains multiple domains ("A" with "B", and "C" with "D"), each domain hosting its own Organizational Units (OUs) like Employees, Sales, and Marketing. The green cubes represent various AD objects such as users, computers, and groups. The arrows indicate the potential for lateral movement of these objects both within domains of the same forest and across domains in different forests. This highlights the complexities and security considerations when managing multiple forests and ensuring secure interactions between them.
2. Moving Vertically
Moving vertically involves shifting an object up or down the hierarchy, between parent and child OUs. For instance, transferring a user from the “Sales” OU to the “East Sales” OU, where “East Sales” is a child of “Sales.”
Why it’s a Weakness:
- Inheritance of Permissions: AD’s hierarchical nature means that child OUs inherit permissions from parent OUs. Moving an object vertically can sometimes result in excessive permissions being inherited from parent OUs, exposing sensitive data or critical resources to users who shouldn’t have access.
- Administrative Overhead: Constantly adjusting permissions and policies as users or objects move vertically can be administratively burdensome and prone to errors, leading to potential security gaps.
3. Complexity and Misconfiguration
- Human Error: Just like map-making, where a tiny error can lead to significant issues, managing AD requires precision. Misconfigurations, such as incorrect permissions or faulty policy applications, are common due to the complex nature of AD, and these can create significant security vulnerabilities.
- Scalability Challenges: As organizations grow, so does the complexity of their AD structure. Without careful planning and management, AD can become unwieldy, making it easier for mistakes and security holes to occur.
4. Lack of Visibility
- Difficulty in Tracking Changes: AD changes, whether lateral or vertical, can be difficult to track without robust monitoring tools. This lack of visibility makes it challenging to detect and respond to unauthorized changes or movements within the directory.
- Auditing Challenges: Proper auditing is essential for security, but the intricate nature of AD means that comprehensive and effective auditing can be hard to maintain, increasing the risk of undetected malicious activities.
5. Dependency on Network Health
- Single Point of Failure: AD is often central to an organization’s network operations. If AD experiences a failure or becomes compromised, it can disrupt the entire network, affecting all connected users and devices.
- Difficulty in Disaster Recovery: Given its critical role, restoring AD from a failure or a security breach can be a complex and time-consuming process, potentially leading to significant operational downtime.
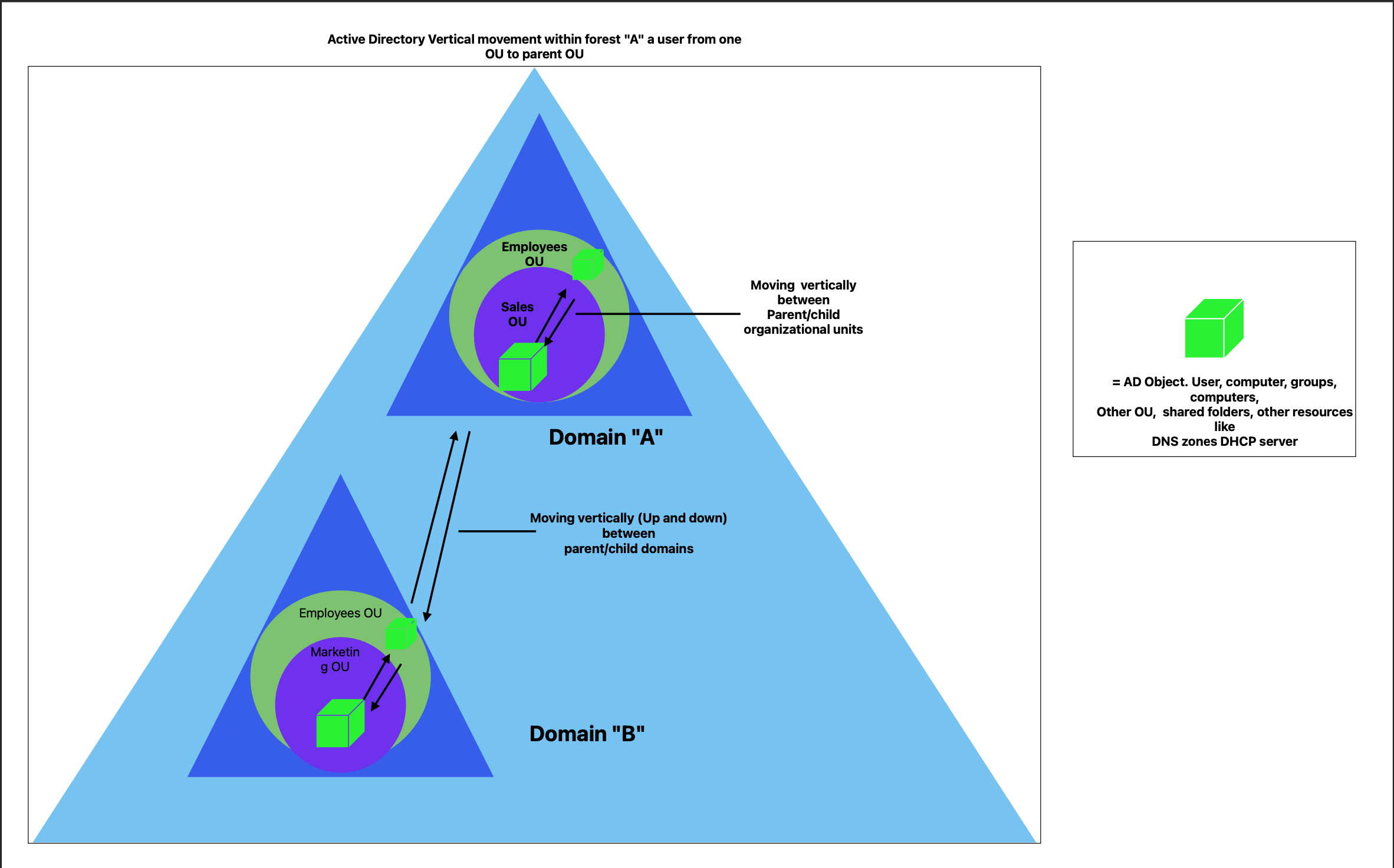 This diagram showcases the vertical movement of Active Directory (AD) objects within the xyz.com forest. It illustrates the hierarchical relationships and movement pathways between parent and child Organizational Units (OUs) within a single domain ("A") and between parent and child domains ("A" and "B").
Key points include:
Movement between parent and child OUs, such as from the Sales OU to the Employees OU within domain "A".
Vertical movement between domain "A" and its child domain "B", which involves transferring AD objects up and down the domain hierarchy.
The green cubes represent AD objects like users, computers, and groups, and the arrows indicate the direction of possible movement. This emphasizes the dynamic nature of AD management, allowing flexible reorganization of resources while maintaining security and administrative controls.
This diagram showcases the vertical movement of Active Directory (AD) objects within the xyz.com forest. It illustrates the hierarchical relationships and movement pathways between parent and child Organizational Units (OUs) within a single domain ("A") and between parent and child domains ("A" and "B").
Key points include:
Movement between parent and child OUs, such as from the Sales OU to the Employees OU within domain "A".
Vertical movement between domain "A" and its child domain "B", which involves transferring AD objects up and down the domain hierarchy.
The green cubes represent AD objects like users, computers, and groups, and the arrows indicate the direction of possible movement. This emphasizes the dynamic nature of AD management, allowing flexible reorganization of resources while maintaining security and administrative controls.
Conclusion
Active Directory (AD) serves as the backbone for many organizations' IT infrastructure, providing a structured and secure way to manage users, computers, and other resources. Just like a complex map, AD's intricate layout allows for efficient organization and access control, but it also presents potential vulnerabilities if not properly managed. Whether considering lateral movements within a domain, vertical shifts across organizational units, or navigating the complexities of multi-forest environments, understanding the fundamental elements of AD is crucial for both administrators and security professionals.
In this article, we have explored the core concepts and structures of Active Directory, drawing parallels to a map-making process to simplify these ideas. By comprehending how domains, OUs, users, groups, and policies interact, we can better appreciate the strengths and potential weaknesses within an AD setup. We also discussed the importance of meticulous configuration and monitoring to prevent security lapses that could arise from lateral and vertical movements within AD.
Stay tuned for our next article, where we will delve deeper into specific exploitation tactics that can be employed within Active Directory environments. We will examine common vulnerabilities, demonstrate real-world attack scenarios, and provide guidance on safeguarding your AD infrastructure against these threats. By building on the foundational knowledge we've covered today, you'll be better equipped to understand and counteract potential exploits in your AD environment.